This blog describes setting up a trust between two domains/forests. In this blog, I used Microsoft Windows Server 2022. A prerequisite to making the 2-way trust work is enabling the necessary firewall ports between the domain controllers.
Check the links below to which network ports are needed for the 2-way trust.
https://learn.microsoft.com/en-us/troubleshoot/windows-server/identity/config-firewall-for-ad-domains-and-trusts
The following tasks need to be executed:
- Setup DNS Conditional Forwarders
- Verify connectivity between the Domain Controllers
- Create the trust
Scenario:
- One Domain Controller (Forest name and Domain name domainA.lan)
- One Domain Controller (Forest name and Domain name domainB.lan)
-
Domain Controller in domainA.lan domain has the following information:
FQDN : srv-ms-dc01.domainA.lan
IP: 192.168.41.10 -
Domain Controller in domainB.lan domain has the following information:
FQDN : srv-ms-dc02.domainB.lan
IP : 192.168.41.50 - Created on both domains a service account with the same password
Note: The domain names in the screenshot differ from those used in the blog.
Setup DNS Conditional Forwarders
This part describes how to create the DNS Conditional Forwarders with PowerShell or through the GUI.
Create DNS Conditional Forwarders with PowerShell
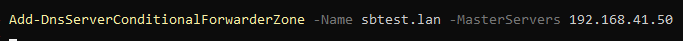
On the Domain Controller in domainA open PowerShell with Administrative rights and execute the following command.
Add-DnsServerConditionalForwarderZone -Name <domain name B> -MasterServers <IP Address DC in domainB>
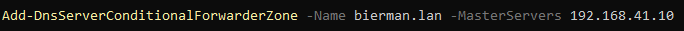
On the Domain Controller in domainB open PowerShell with Administrative rights and execute the following command:
Add-DnsServerConditionalForwarderZone -Name <domain name A> -MasterServers <IP Address DC in domainA>
The next step is verifying if the DNS Conditional Forwarders resolve the addresses.
Open the Domain Controller in DomainA DNS Manager Snapin from the Administrative Tools. Expand the Conditional Forwarders.
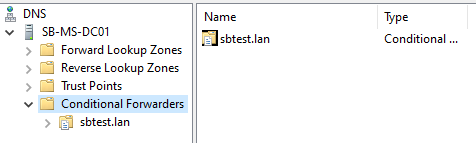
Right-click the Domain Name and select Properties.
Select Edit from the screenshot below.
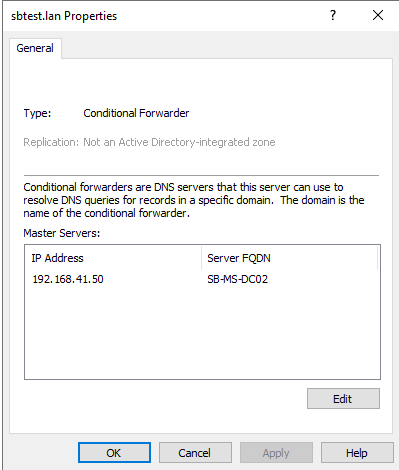
When the validation shows OK the Conditional Forwarder is working correctly.
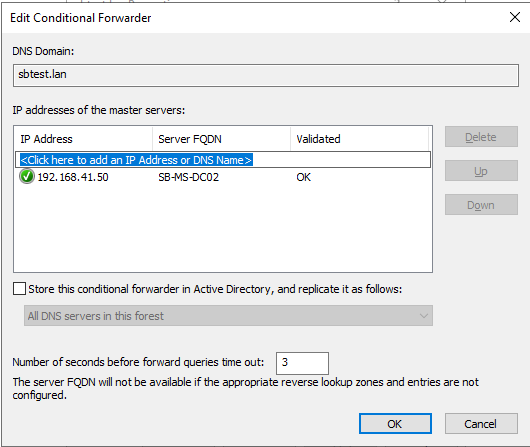
Execute this test also on the Domain Controller of domainB.
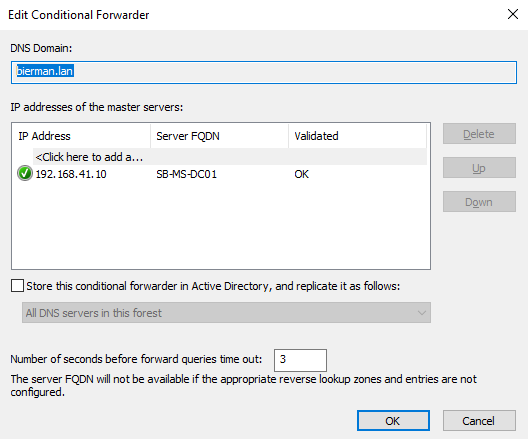
When both Conditional Forwarders are correctly validated, we continue with the Trust.
Create DNS Conditional Forwarders through the GUI
Open the DNS Manager on both Domain Controllers in both Domains.
Right-click on the Conditional Forwarders and select New Conditional Forwarder.
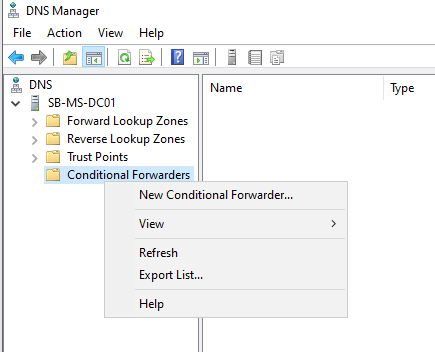
Enter the domain name (DomainB.lan) and enter the IP Address of the Domain Controller in domainB.
Select the option Store this conditional forwarder in Active Directory, and replicate it as follows. Leave the configuration All DNS servers in this forest as it is.
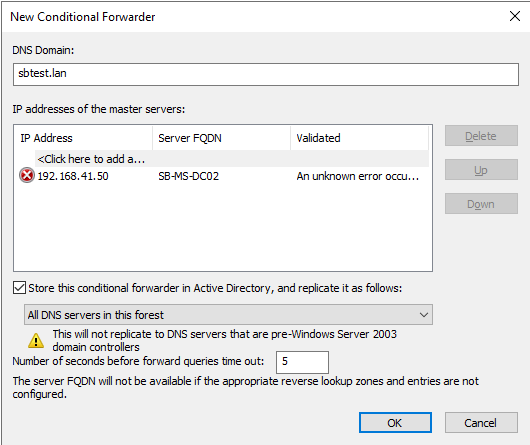
Select OK to store the newly created Conditional Forwarder. The validation is not executed yet.
The new conditional forwarder is created. Right-click the domain name and select Properties.
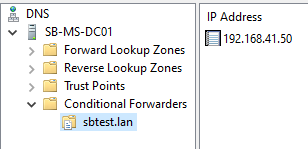
The new created conditional forwarder opens and select Edit.
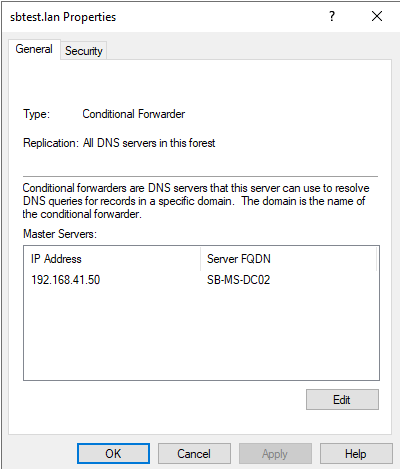
If the validation is correct the validation shows OK.
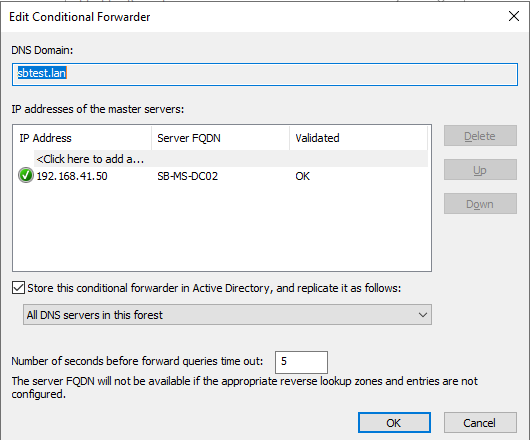
Execute the same steps on the Domain Controller in domainB.
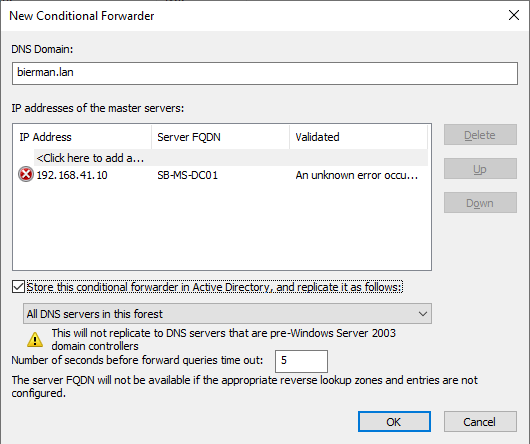
Use the name of domainA and enter the IP Address of the Domain Controller of domainA. Multiple IP Addresses of Domain Controllers could be added.
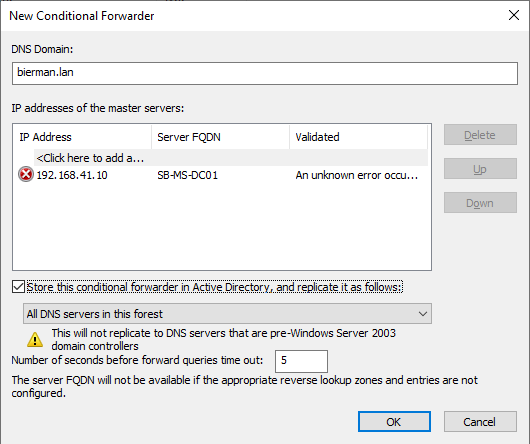
After the creation of the conditional forwarder re-open to check if the validation is succeeded.
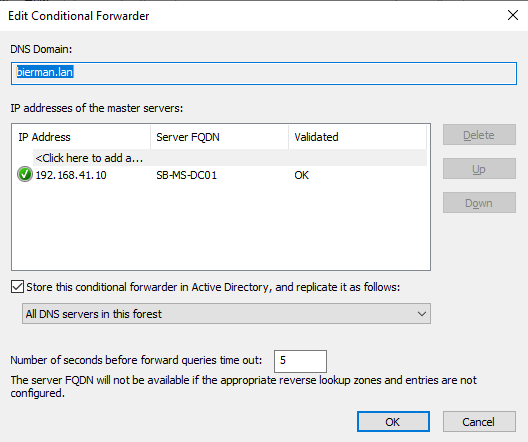
The Conditional Forwarders are now created on both domains.
Create the two-way trust between the Forest/Domain
The next step is creating the two-way trust between the 2 forests/domains.
Create the two-way trust with PowerShell
Netdom cannot be used to create a forest trust between two AD DS Forests. To create a cross-forest trust between two AD DS Forests use the script below.
Source: http://technet.microsoft.com/en-us/library/cc835085%28v=ws.10%29.aspx
The option CreateTrustRelationShip can hold 3 options:
- Bidirectional
- Inbound
- Outbound
Because we are creating a two-way trust the option should be Bidirectional.
Script:
# Change following parameters
$strRemoteForest = "<domainB>"
$strRemoteAdmin = "domainB\<username>"
$strRemoteAdminPassword = "<password>
$remoteContext = New-Object -TypeName "System.DirectoryServices.ActiveDirectory.DirectoryContext" -ArgumentList @( "Forest", $strRemoteForest, $strRemoteAdmin, $strRemoteAdminPassword)
try {
$remoteForest = [System.DirectoryServices.ActiveDirectory.Forest]::getForest($remoteContext)
#Write-Host "GetRemoteForest: Succeeded for domain $($remoteForest)"
}
catch {
Write-Warning "GetRemoteForest: Failed:`n`tError: $($($_.Exception).Message)"
}
Write-Host "Connected to Remote forest: $($remoteForest.Name)"
$localforest=[System.DirectoryServices.ActiveDirectory.Forest]::getCurrentForest()
Write-Host "Connected to Local forest: $($localforest.Name)"
try {
$localForest.CreateTrustRelationship($remoteForest,"Bidirectional")
Write-Host "CreateTrustRelationship: Succeeded for domain $($remoteForest)"
}
catch {
Write-Warning "CreateTrustRelationship: Failed for domain $($remoteForest)`n`tError: $($($_.Exception).Message)"
}
Open the Active Directory Domains and Trusts on the Domain Controller in domainA. Right-click the domain name and select properties.
Select the tab Trusts and check if domainB is added in the Outgoing and Incoming trust. Check this also on the Domain Controller in domainB.
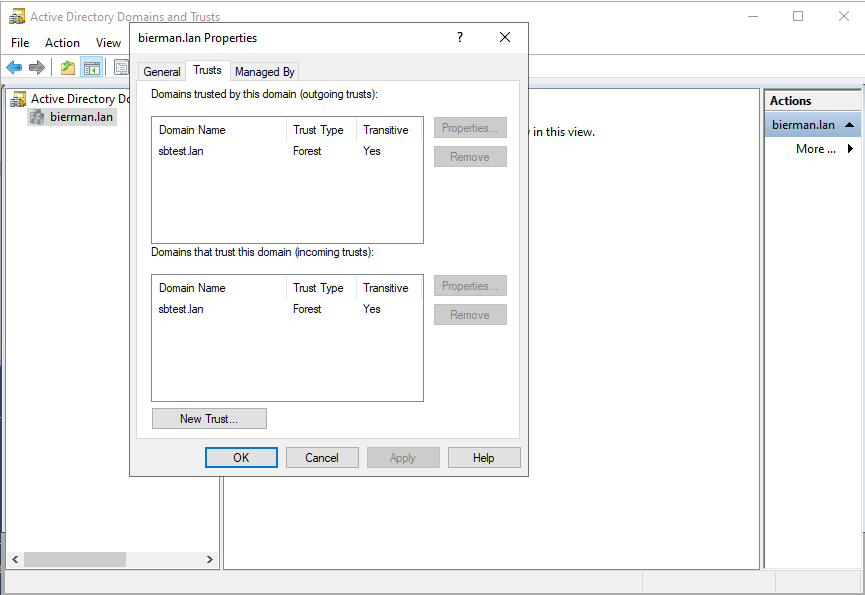
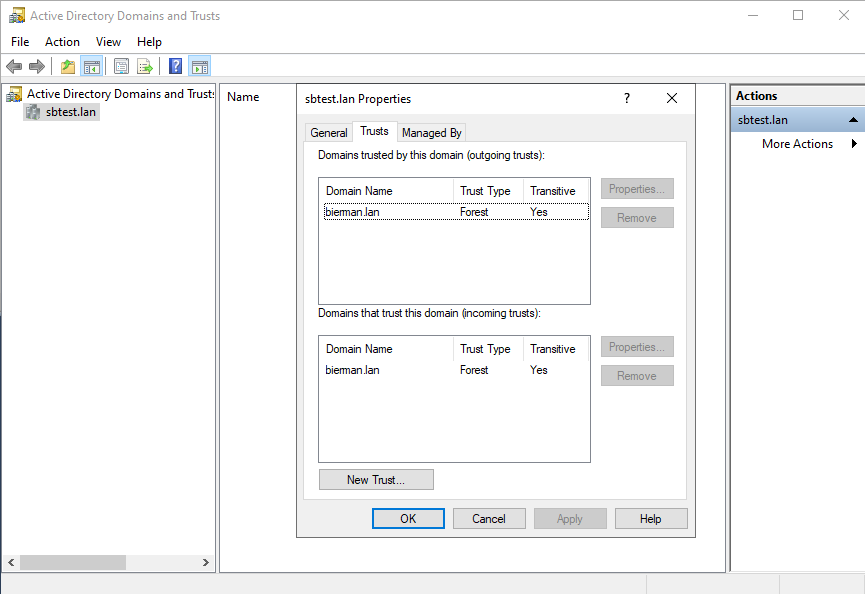
If both Domain Controllers show the Trust the two-way trust is successfully created.
Create the two-way trust through the GUI
Open the Active Directory Domains and Trusts Snap-in from the Administrative Tools on the Domain Controller in domainA.
Right-click the domain name and select Properties.
Select the tab Trusts.
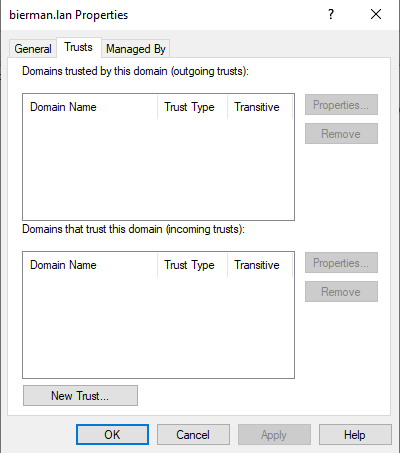
Select New Trust.
Select Next in the Welcome window.
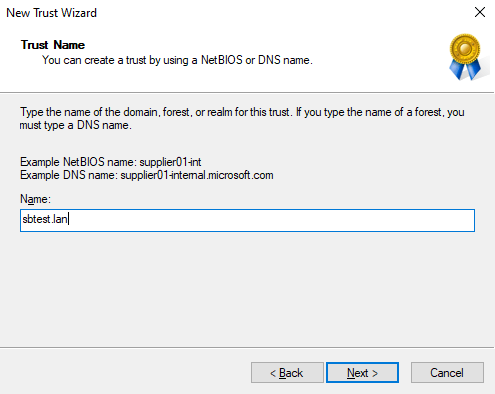
Enter the domainB name in the field and select Next to continue.
Select Forest trust and select Next to continue.
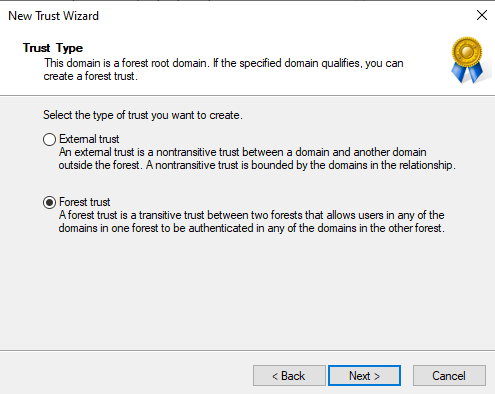
Select Two-way and select Next to continue.
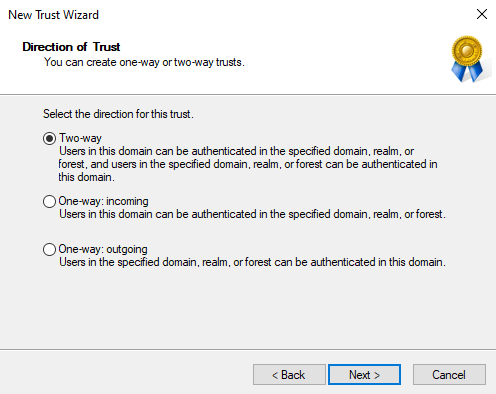
Select Both this domain and the specified domain and select Next to continue.
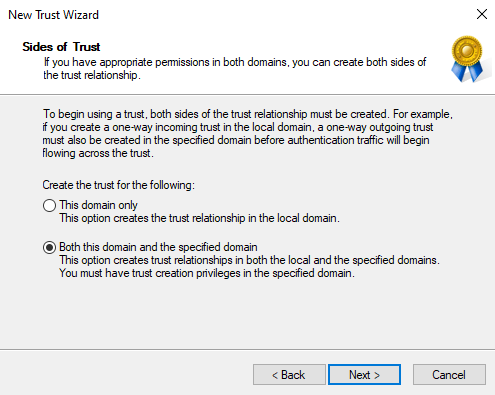
Enter the credentials of an admin account from domainB and select Next to continue.
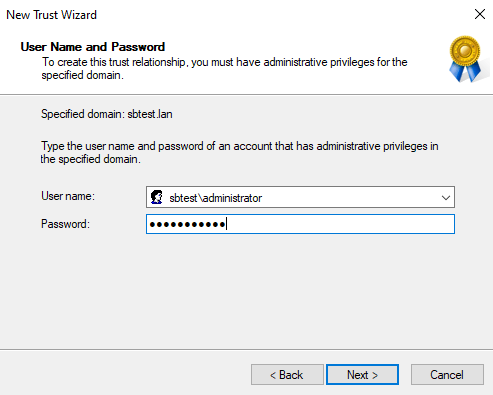
Select Forest-wide authentication and select Next to continue. Execute this twice.
Select Next in the Trust Selections Complete window.
Select Next in the Trust Creation Complete window.
Select Yes, confirm the outgoing trust and select Next to continue.
Execute this also for the Incoming Trust.
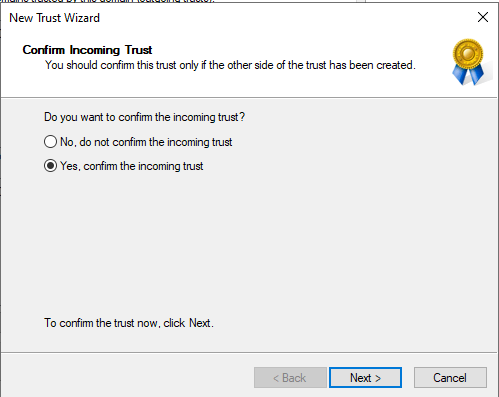
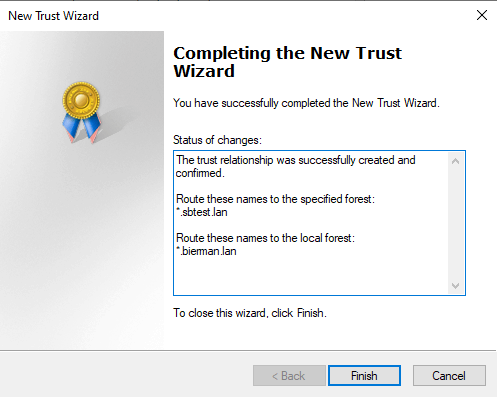
Select Finish to finalize the two-trust configuration.
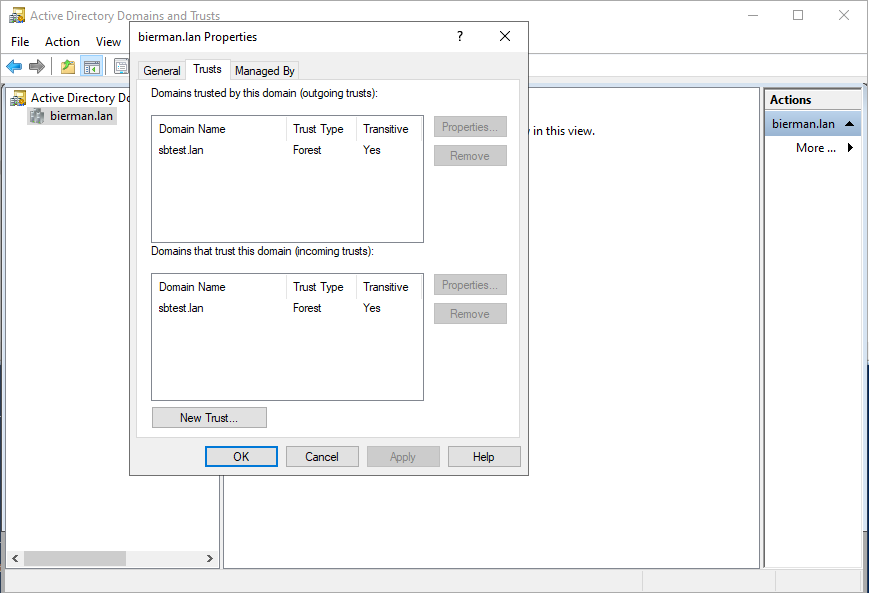
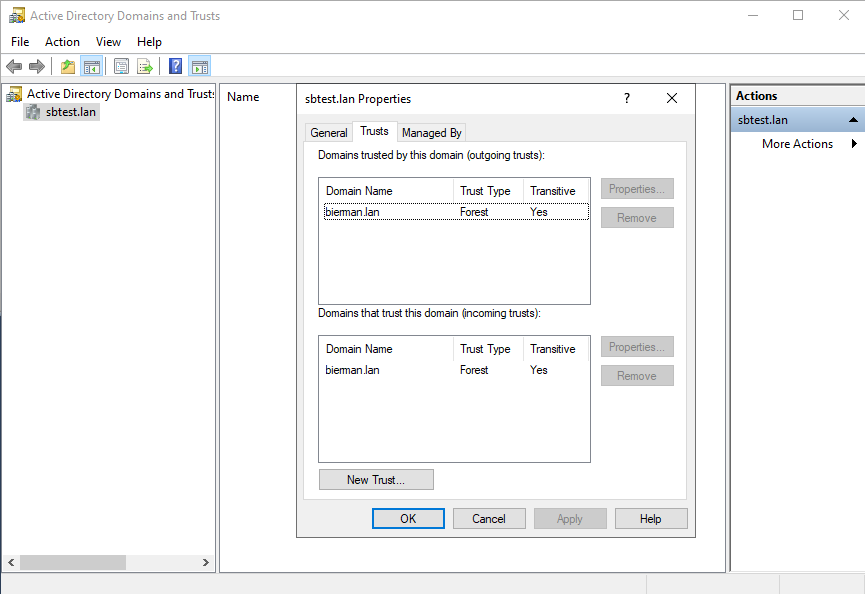
Check on both Domain Controllers in the Active Directory Domains and Trusts Snap-in if the trust is created on both Incoming and Outgoing.




Pingback: Ivanti Identity Director Web Portal login with 2-way trust Active Directory forests/domains - Automated Vision
it will be nice if you can fix the missing pictures
Sorry for the inconvenience. Fixed the issue with the missing pictures.
I am looking for a way to create a one-way outbound external trust (NOT transitive) using PowerShell. I have tried using the “Outbound” argument with $localForest.CreateTrustRelationship, but that still creates a one-way *Forest* trust, which is transitive. Is there a way to create an External trust using PowerShell?
Thanks for any advice!